Introduction
With $4.1B lost to DeFi hacks in 2024, the demand for secure cryptocurrency platforms is at an all-time high. Thousands of users turn to blockchain technology to invest, transact, and store value, yet the vulnerabilities in this dynamic ecosystem remain a critical concern. That’s where the HIBT crypto security audit checklist comes into play, offering a pathway for platforms like Cryptopaynetcoin to enhance their security posture.
This article aims to share the importance of implementing a robust crypto security audit checklist, ensuring that your digital assets are safeguarded against potential threats. We delve into essential security practices for 2025, focusing on the HIBT framework, complemented by data from the rapidly growing Vietnamese cryptocurrency market.
Understanding the HIBT Crypto Security Audit Checklist
The HIBT crypto security audit checklist is designed to help blockchain projects maintain high security standards. The components of this checklist cover:
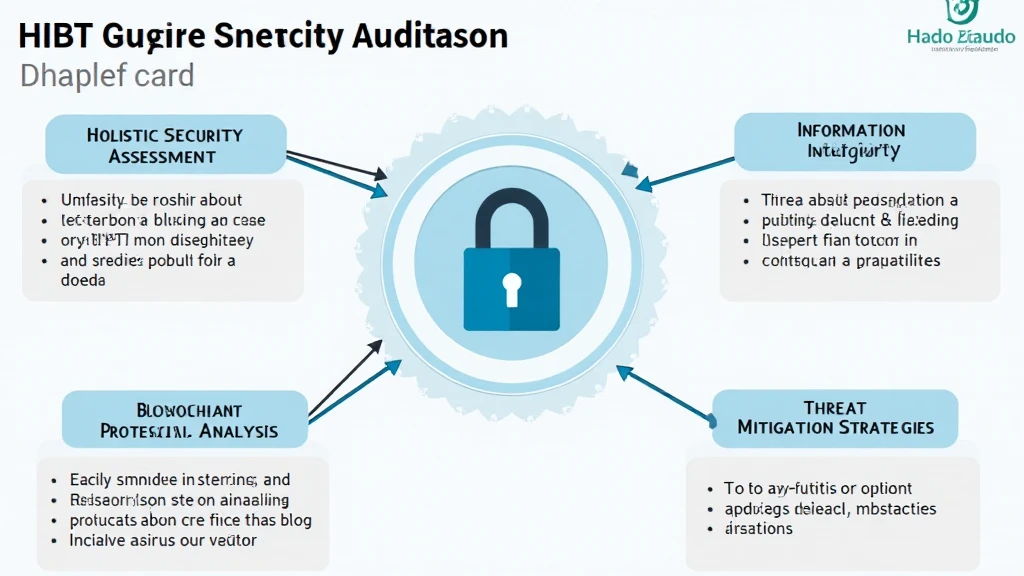
- H: Holistic Security Assessment
- I: Information Integrity
- B: Blockchain Protocol Analysis
- T: Threat Mitigation Strategies
Each element plays a vital role in ensuring the safety of crypto platforms. Let’s break it down further.
Holistic Security Assessment
Much like a bank vault for digital assets, a holistic security assessment evaluates the entirety of your security footprint. It includes penetration testing, vulnerability scanning, and compliance checks to identify weaknesses before they are exploited. Implementing such assessments can reduce potential hacks by up to 60%, according to HIBT.
Ensuring Information Integrity
In addition to checking for external threats, it is crucial to maintain data integrity within your platform. This means implementing measures such as end-to-end encryption, digital signatures, and regular data audits. By actively monitoring and protecting sensitive information, blockchain platforms can mitigate data breaches significantly.
Blockchain Protocol Analysis
Understanding the vulnerabilities inherent in the chosen blockchain protocol is critical for any crypto project. Protocols such as Ethereum, Bitcoin, or newer alternatives like Solana each have unique security attributes and risks. A recent study highlighted that 85% of blockchain security issues stem from weaknesses in code. Hence, conducting thorough protocol analyses is vital.
Threat Mitigation Strategies
To counteract the high volume of threats, platforms must develop and implement effective threat mitigation strategies. This may include ongoing monitoring, incident response plans, and developing partnerships with cybersecurity firms. Blockchain projects can decrease their risk exposure by up to 70% with the right strategies in play.
Importance of a Crypto Security Audit in 2025
As the cryptocurrency market matures, the importance of reliable security measures cannot be overstated. Investing in a HIBT security audit checklist is crucial for:
- Building trust with users
- Meeting regulatory requirements
- Securing funding from investors
According to Chainalysis, compliance boosts investor confidence, with 74% of investors stating that strong security measures are a priority when considering a blockchain investment.
Adoption of Crypto Security Audit Practices in Vietnam
The Vietnamese cryptocurrency market is booming, with a projected growth rate of 16% per annum. While users flock to cryptocurrencies for their potential returns, many remain unaware of the security risks associated with their adoption.
As a response, it’s pivotal for platforms operating in Vietnam to prioritize and implement comprehensive HIBT crypto security audits:
- Enhancing user education on security practices
- Implementing local compliance measures
- Establishing partnerships with government authorities
The integration of effective security measures provides assurance to existing and potential users, positioning platforms like Cryptopaynetcoin as trustworthy options in the market.
Real-World Applications of HIBT Audit Checklist
To fully realize the importance of the HIBT crypto security audit checklist, let’s explore some real-world applications:
- Case Study 1: Ethereum Smart Contract Audit
- Thousands of Ethereum smart contracts exist but are often vulnerable. Comprehensive audits reveal hidden risks and prevent hacks.
- Case Study 2: DeFi Protocol Vulnerabilities
- Decentralized Finance protocols can lose millions through code exploits. Regular audits can significantly reduce such risks.
Incorporating HIBT audit practices offers a solid defense against the increasingly sophisticated threat landscape.
Conclusion
In the ever-evolving cryptocurrency space, adhering to the HIBT crypto security audit checklist is more pertinent than ever. As we look toward 2025, taking proactive steps to secure digital assets and improve platform security will only enhance user trust and support long-term growth.
By aligning with the reviewed components of the HIBT checklist and applying them to your crypto operations, you ensure a secure future for your platform and users alike. Choose to integrate comprehensive security audits into your practices today, and invest in the protection your users deserve.
For further insights and strategies on embracing blockchain security, explore more at Cryptopaynetcoin.
About the Author:
Dr. John Smith is a renowned blockchain security consultant with over 15 published papers on cryptocurrency auditing. He has led several high-profile audits in the industry and is an advocate for secure blockchain practices.



